Hands-on Secure Coding
Training Platform
SecureFlag has revolutionized the approach to secure coding training. With SecureFlag’s hands-on labs, participants learn in virtualized environments using the tools they know and love.


Labs & Paths
Developers have access to a continuously updated library of Labs and Learning Paths based on real-world vulnerabilities.
SecureFlag’s Labs teach participants how to identify and remediate the most prevalent security issues by doing instead of simply just seeing.
Labs run in real, virtualized development environments, and participants learn using the same tools they use at work.
Training Plan
With SecureFlag, organizations can create Training Plans and automatically assign participants training throughout the program.
SecureFlag automatically adapts topics and difficulty levels based on each individual user's previous results.
Organizations can effortlessly implement iterative and individualized training to fill competence gaps.
Teams
Group users together and watch the friendly competition unfold on leaderboards.
Team Managers can set up training tasks and keep abreast of participants’ progress.
Appointing Team Managers on board is a game-changer; they can have a profound impact on the effectiveness of the program by ensuring the program runs smoothly and participants are on track. SecureFlag offers free licenses for all administrative users who don’t partake in any training.
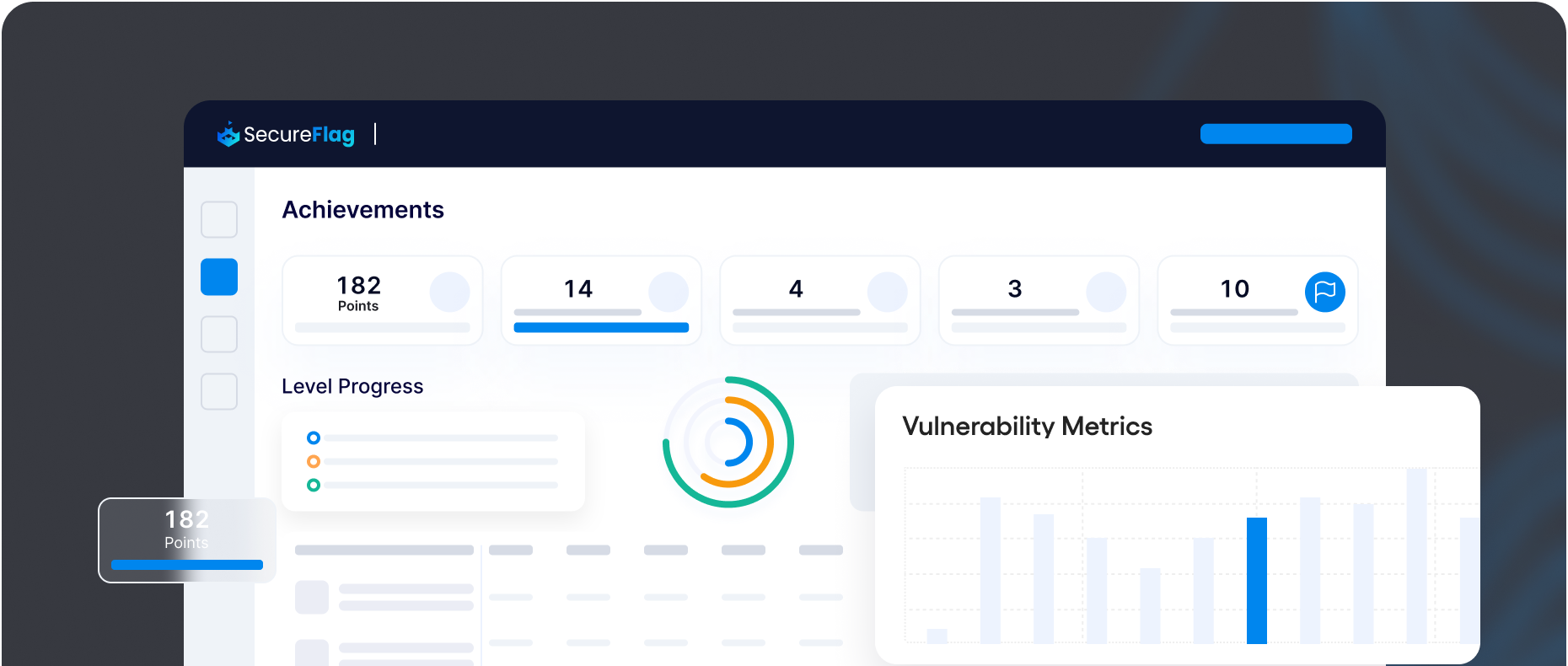
Achievements and Metrics
SecureFlag measures participants' real secure coding competence with powerful, in-depth analytics and on-demand reports. Managers can effortlessly review areas to focus on via a dashboard that displays actionable information derived from individual, team, and organization-wide training results.

Customer Success
Experience a personalized onboarding journey with a Customer Success Manager (CSM) by your side.
From the initial onboarding and implementation process through to uniquely crafted Training Plans and support in tuning the program throughout, our CSM ensures ongoing success.
Your CSM will also assist in the organization of exclusive events like Tournaments and Secure Coding Month!
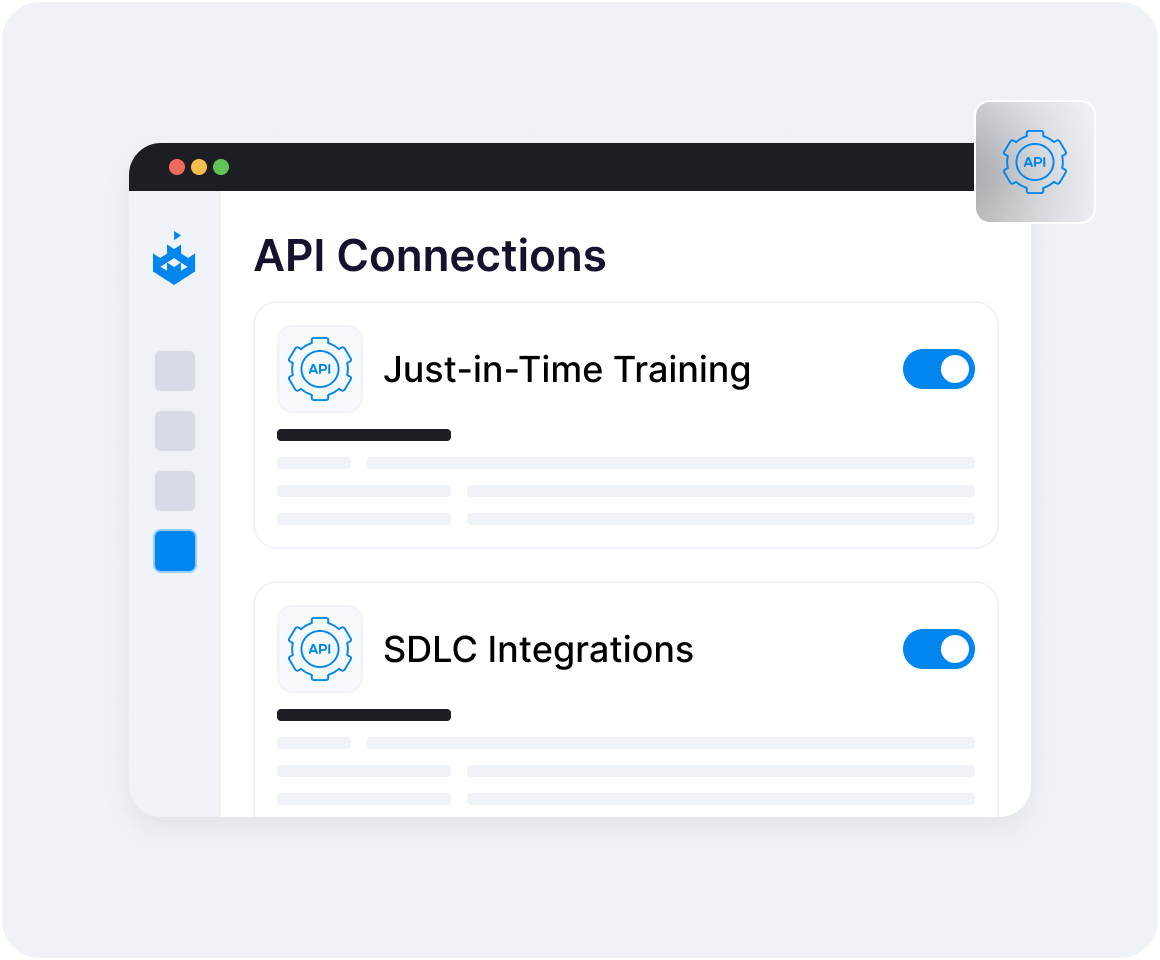
Powerful Integrations
Our Just-In-Time Training plugins enrich security remediation tickets, offering developers immediate guidance on vulnerability resolution, coupled with relevant hands-on labs for practical application.
For organizations using Learning Management Systems, SecureFlag’s integrations ensure all assignments and results are centralized.
Additionally, SecureFlag provides hundreds of APIs to cater to more complex integrations.
Contact us to book a Free Demo!